System Backup: 7 Ultimate Strategies for Total Data Protection
In today’s digital-first world, losing critical data can mean losing everything. A solid system backup isn’t just smart—it’s essential. Discover the ultimate strategies to protect your data like a pro.
What Is a System Backup and Why It Matters

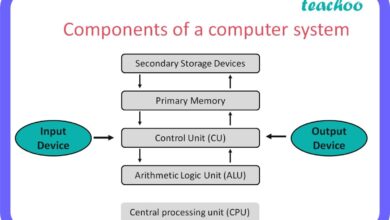
A system backup refers to the process of copying and archiving computer data so it can be restored in the event of data loss. This loss could stem from hardware failure, malware attacks, accidental deletion, or natural disasters. In essence, a system backup acts as a safety net for your digital life.
Defining System Backup
At its core, a system backup involves creating a duplicate of your operating system, applications, settings, and personal files. Unlike file-level backups that only save user documents, a full system backup captures the entire state of your machine. This means if your computer crashes, you can restore not just your files, but your entire environment—exactly as it was.
- Includes OS, installed programs, configurations, and user data
- Can be performed locally, in the cloud, or via hybrid models
- Enables complete system recovery after failure
According to the National Institute of Standards and Technology (NIST), regular system backups are a foundational component of any cybersecurity framework.
Common Causes of Data Loss
Data loss doesn’t always come from dramatic events. In fact, everyday actions and oversights are often to blame. Understanding the root causes helps emphasize why a reliable system backup strategy is non-negotiable.
Hardware failure: Hard drives fail.SSDs wear out.It’s not a matter of if, but when.Malware and ransomware: Cybercriminals encrypt your data and demand payment..
Without a backup, you’re at their mercy.Human error: Accidentally deleting files or formatting drives is more common than you think.Natural disasters: Fires, floods, and power surges can destroy physical devices.Software corruption: Updates gone wrong or buggy applications can render systems unusable.”The best disaster recovery plan starts with a reliable backup.” — TechTargetTypes of System Backup: Full, Incremental, and DifferentialNot all system backups are created equal.Different backup types serve different purposes and come with their own trade-offs in terms of speed, storage, and recovery time.Choosing the right type depends on your needs, resources, and risk tolerance..
Full System Backup
A full system backup copies every single file and folder on your system, including the operating system, applications, and user data. It’s the most comprehensive form of backup and serves as the foundation for other backup types.
- Provides complete data protection
- Takes the longest time and consumes the most storage
- Ideal for initial backups or critical system snapshots
For example, if you’re about to perform a major system upgrade, a full system backup ensures you can roll back to a stable state if something goes wrong. Tools like Macrium Reflect and Acronis True Image specialize in full system imaging.
Incremental Backup
An incremental system backup only saves the data that has changed since the last backup—whether that was a full or another incremental backup. This makes it fast and storage-efficient.
- Backs up only new or modified files
- Requires less time and disk space
- Restoration requires the full backup plus all subsequent incrementals
While efficient, this method can be risky. If one incremental file is corrupted, the entire chain may be compromised. It’s best used in environments with limited bandwidth or storage but requires careful management.
Differential Backup
Differential backups capture all changes made since the last full backup. Unlike incremental backups, they don’t reset after each backup, so each differential file grows larger over time.
- Easier and faster to restore than incremental backups
- Requires more storage than incremental but less than full
- Restoration only needs the last full backup and the latest differential
Differential backups strike a balance between speed and reliability, making them ideal for businesses that need quick recovery without the complexity of managing long incremental chains.
Best Practices for Effective System Backup
Having a backup is one thing; having an effective one is another. Many people think they’re protected until they try to restore and realize their backup is incomplete, outdated, or corrupted. Follow these best practices to ensure your system backup actually works when you need it.
Follow the 3-2-1 Backup Rule
The 3-2-1 rule is a gold standard in data protection. It states: keep three copies of your data, on two different media, with one copy stored offsite.
- Three copies: Your primary data + two backups
- Two media: For example, an external hard drive and a cloud service
- One offsite: Protects against local disasters like fire or theft
This strategy minimizes single points of failure and ensures redundancy. Cloud services like Backblaze and Google Drive make offsite storage accessible and affordable.
Schedule Regular Backups Automatically
Manual backups are unreliable. People forget. Systems change. The only way to ensure consistency is automation.
- Set up daily or weekly backups depending on data criticality
- Use built-in tools like Windows Backup and Restore or macOS Time Machine
- Leverage third-party software with scheduling features (e.g., Veeam, EaseUS Todo Backup)
Automated system backup ensures that even if you’re busy, your data is protected. It also reduces human error and ensures version control.
Test Your Backups Regularly
A backup you’ve never tested is a backup you can’t trust. Many organizations discover too late that their backups are incomplete or corrupted.
- Perform periodic restore tests on a separate machine
- Verify file integrity and system functionality
- Document test results and update procedures accordingly
The SANS Institute recommends testing backups at least quarterly. This practice builds confidence in your disaster recovery plan.
Cloud vs. Local System Backup: Pros and Cons
One of the biggest decisions in designing a system backup strategy is choosing between cloud-based and local (on-premise) solutions. Each has strengths and weaknesses, and the best approach often involves a hybrid model.
Advantages of Cloud-Based System Backup
Cloud backups have surged in popularity due to their convenience, scalability, and accessibility.
- Automatic syncing: Files are backed up in real-time or on a schedule without user intervention.
- Offsite protection: Immune to local disasters like fires or floods.
- Scalable storage: Pay only for what you use, with easy upgrades.
- Access from anywhere: Retrieve files from any device with internet access.
Services like Dropbox Business, OneDrive, and AWS Backup offer enterprise-grade encryption and compliance features.
Drawbacks of Cloud-Based System Backup
Despite their benefits, cloud backups aren’t perfect. They come with limitations that can impact performance and security.
- Internet dependency: Slow upload speeds can delay backups.
- Ongoing costs: Monthly fees can add up over time.
- Privacy concerns: Data is stored on third-party servers, raising compliance issues.
- Recovery time: Large restores may take hours or days depending on bandwidth.
For sensitive data, some organizations prefer to keep backups in-house to maintain full control.
Benefits of Local System Backup
Local backups, such as those stored on external hard drives or network-attached storage (NAS), offer speed and control.
- Fast backup and restore: No internet bottleneck; transfers happen over local networks.
- One-time cost: After purchasing hardware, there are no recurring fees.
- Full data control: Ideal for regulated industries like healthcare and finance.
- Offline security: Not exposed to online threats when disconnected.
However, local backups are vulnerable to physical damage and theft, which is why they should never be the only line of defense.
Top Tools and Software for System Backup
Choosing the right tool can make or break your system backup strategy. The market is flooded with options, from free utilities to enterprise-grade platforms. Here’s a breakdown of the most reliable solutions.
Free System Backup Tools
For individuals and small businesses, free tools can provide robust protection without breaking the bank.
- Macrium Reflect Free: Offers disk imaging and cloning for Windows. Supports automatic scheduling and compression.
- Clonezilla: Open-source tool for disk cloning and imaging. Great for tech-savvy users.
- Time Machine (macOS): Built-in solution for Mac users. Simple setup and seamless integration.
While free tools are cost-effective, they may lack advanced features like cloud sync or centralized management.
Paid System Backup Solutions
For businesses and power users, paid software offers enhanced reliability, support, and scalability.
- Acronis True Image: Combines local and cloud backup with ransomware protection and blockchain-based file notarization.
- Veeam Backup & Replication: Industry leader for virtual and physical environments. Ideal for enterprises using VMware or Hyper-V.
- Cohesity DataProtect: Modern platform for backup, recovery, and data management across hybrid environments.
These tools often include features like deduplication, encryption, and AI-driven anomaly detection, making them worth the investment for critical systems.
Enterprise-Grade Backup Platforms
Large organizations need solutions that can scale across thousands of devices while ensuring compliance and fast recovery.
- Veritas NetBackup: Supports multi-cloud, on-premise, and hybrid environments. Offers centralized policy management.
- Dell PowerProtect: Integrates with existing IT infrastructure and provides end-to-end data protection.
- Commvault Complete Backup & Recovery: Unified platform for data backup, archiving, and disaster recovery.
These platforms often integrate with SIEM (Security Information and Event Management) systems and support regulatory standards like HIPAA, GDPR, and PCI-DSS.
How to Perform a System Backup on Windows and macOS
Both major operating systems offer built-in tools for system backup. Knowing how to use them effectively can save you time and stress in an emergency.
Windows: Using Built-in Backup Tools
Windows includes several tools for system backup, including File History and System Image Backup.
- Navigate to Control Panel > System and Security > Backup and Restore (Windows 7)
- Click “Set up backup” to configure your destination (external drive or network location)
- Choose between saving everything or custom folders
- Enable “Let me choose” to include a system image for full recovery
Note: Microsoft has deprecated System Image Backup in Windows 11, pushing users toward third-party tools or cloud solutions. However, it remains available in Windows 10 via legacy settings.
macOS: Leveraging Time Machine
Time Machine is one of the most user-friendly system backup tools available.
- Connect an external drive or use a Time Capsule
- Go to System Settings > General > Time Machine
- Select “Back Up Automatically” and choose your drive
- Time Machine will perform hourly, daily, and weekly backups automatically
You can browse backups using the Time Machine interface, restoring individual files or the entire system with ease.
Third-Party Tools for Cross-Platform Backup
For users with mixed environments, third-party tools offer unified backup solutions.
- AOMEI Backupper: Supports Windows and macOS with imaging, cloning, and sync features.
- Paragon Backup & Recovery: Offers advanced options like bare-metal restore and encryption.
- Carbon Copy Cloner: macOS-focused but highly reliable for bootable backups.
These tools often provide more flexibility than built-in options, especially for advanced users.
Disaster Recovery and System Restore: What Comes After Backup
A system backup is only half the battle. The real test comes during recovery. A well-designed disaster recovery plan ensures you can restore operations quickly and minimize downtime.
Creating a Disaster Recovery Plan
A disaster recovery plan (DRP) outlines the steps to recover IT systems after a disruption. It should include:
- Inventory of critical systems and data
- Recovery time objectives (RTO) and recovery point objectives (RPO)
- Roles and responsibilities during recovery
- Step-by-step restoration procedures
- Communication protocols
According to IBM, organizations with a documented DRP recover 70% faster than those without.
Performing a System Restore from Backup
Restoring from a system backup varies by platform and tool, but the general process includes:
- Boot from a recovery drive or installation media
- Select “Repair your computer” or equivalent option
- Choose “Restore from a system image” or backup file
- Follow prompts to overwrite the current system with the backup
It’s crucial to verify that all drivers, applications, and settings are intact after restoration.
Minimizing Downtime with Bare-Metal Restore
Bare-metal restore allows you to recover an entire system to new hardware, even if the original machine is destroyed.
- Requires a complete system image backup
- Can be performed on dissimilar hardware with compatible tools
- Essential for business continuity in catastrophic scenarios
Tools like Acronis and Veeam support universal restore, making it easier to migrate to new hardware without reinstalling everything from scratch.
Emerging Trends in System Backup Technology
The world of system backup is evolving rapidly. New technologies are making backups faster, smarter, and more secure than ever before.
AI-Powered Backup Solutions
Artificial intelligence is being integrated into backup platforms to detect anomalies, predict failures, and optimize storage.
- AI can identify unusual file access patterns that may indicate ransomware
- Machine learning models predict disk failure before it happens
- Smart deduplication reduces storage needs by identifying redundant data
For example, Cohesity’s AI engine scans backups for signs of malware, providing an extra layer of security.
Blockchain for Backup Integrity
Blockchain technology is being used to ensure the authenticity and immutability of backup files.
- Each backup is cryptographically signed and timestamped
- Prevents tampering and ensures data integrity
- Useful for compliance and legal evidence
Acronis uses blockchain notarization to verify that backups haven’t been altered, adding trust in high-stakes environments.
Zero-Trust Backup Architectures
With rising cyber threats, the zero-trust model is being applied to backup systems.
- Assumes no user or device is trusted by default
- Requires multi-factor authentication for backup access
- Encrypts data both in transit and at rest
This approach minimizes the risk of unauthorized access and ensures that even if backup servers are compromised, the data remains protected.
What is the difference between a file backup and a system backup?
A file backup only saves user documents like photos, videos, and spreadsheets. A system backup, on the other hand, includes the entire operating system, installed applications, settings, and user data. This allows for a complete restoration of the computer to a previous state, not just individual files.
How often should I perform a system backup?
For most users, a weekly system backup is sufficient. However, if you work with critical data or make frequent system changes, daily backups are recommended. Combine this with daily file-level backups for optimal protection.
Can I restore a system backup to a different computer?
Yes, but it depends on the backup tool and hardware compatibility. Some software, like Acronis and Veeam, supports “universal restore,” allowing you to restore a system image to dissimilar hardware. However, driver conflicts may occur, so it’s best to test the process beforehand.
Is cloud backup safe for sensitive data?
Yes, if you use a reputable provider with strong encryption (AES-256) and compliance certifications. Always enable two-factor authentication and consider encrypting data locally before uploading. Avoid storing unencrypted sensitive data in the cloud.
What should I do if my backup fails?
First, check the error logs to identify the cause—common issues include insufficient storage, connectivity problems, or corrupted files. Resolve the issue, then rerun the backup. If the problem persists, consider switching to a different backup method or tool. Always have a secondary backup strategy in place.
System backup is not a luxury—it’s a necessity in our data-driven world. From understanding the different types of backups to choosing the right tools and planning for disaster recovery, every step matters. By following the 3-2-1 rule, automating your backups, and testing them regularly, you can ensure your data survives any catastrophe. As technology evolves, so too must our backup strategies, embracing AI, blockchain, and zero-trust models to stay ahead of emerging threats. Don’t wait for disaster to strike—start building your resilient system backup plan today.
Further Reading: